Crypto is short for cryptography. Recently, the scope of its meaning has expanded to include a broader range of definitions. These meanings can include basic cryptographic concepts or an entire ecosystem of crypto-enabled technologies, enterprises, and communities.
Cryptography is a multidisciplinary field that is focused on securing and validating information. It borrows and applies concepts from mathematics, computer science, electrical engineering, and physics.
The applications of crypto are constantly widening, and at their core, they implement one or a combination of the following features:
- authentication,
- data confidentiality,
- data integrity,
- non-repudiation, and
- data compression.
The components of cryptography that underpin most applications are hashing functions, encryption, signatures, and random number generators.
Hashing Functions
Hashing functions are one of the most underrated innovations in the information technology domain. They are at the core of many systems, including but not limited to: keeping passwords safe; validating data integrity; allowing distributed systems to scale in a deterministic way; proving the existence of specific data without revealing its content; deduplicating content without checking it; detecting storage or communicating errors, etc.
Hashing functions map an arbitrary input to an output in a deterministic way so that an (input, output) pair is always the same. Reversing the process and obtaining the input from the output should be nearly impossible or highly unspecific.
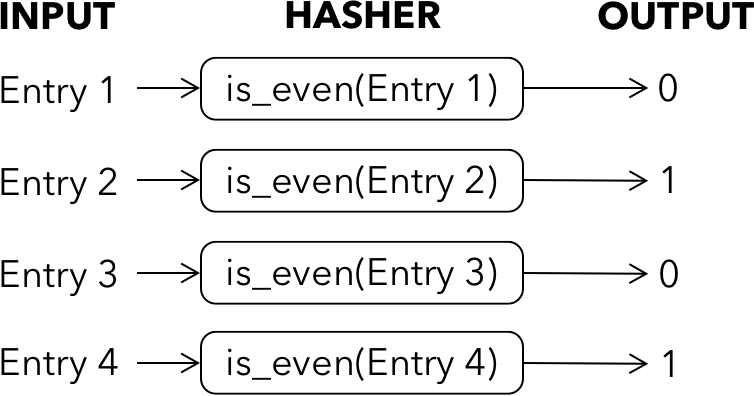
One of the most straightforward hashing functions is checking if a number is even or odd and outputting 0 or 1, respectively. This simple example couple be applied to easily split (or shard) a uniformly distributed dataset into two sets, allowing for the data to be partitioned into two different machines.
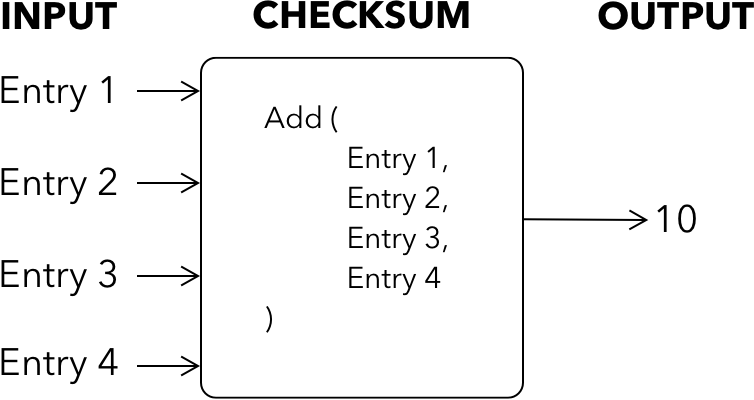
An intermediate hashing function could add all the numbers together and produce a “checksum” of the dataset. When transmitting these numbers to another entity, this checksum can also be provided, and the receiver could run the same addition and check if their sum also matches. If it does, then the receiver can have higher confidence that the dataset was correctly received.
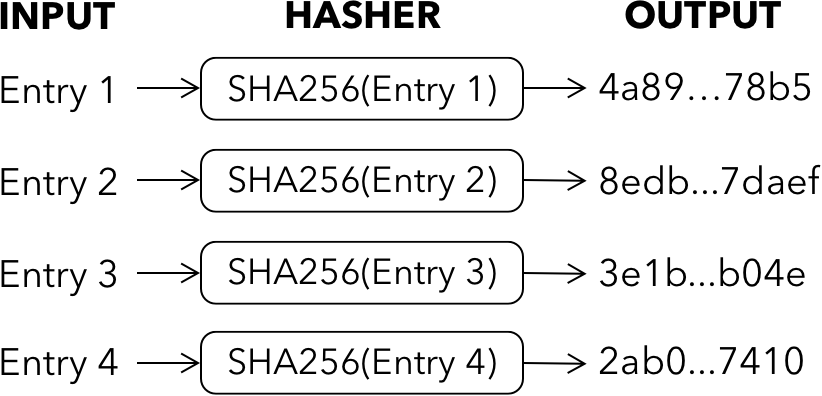
More advanced hashing functions can have the crucial property of virtually guaranteeing that an input is unique for a particular output. With these types of hashing functions, it becomes practically impossible to obtain a matching (input, output) given only a specific output. For such cases, if someone can compute a particular output, it is almost certain that they have access to a unique input.
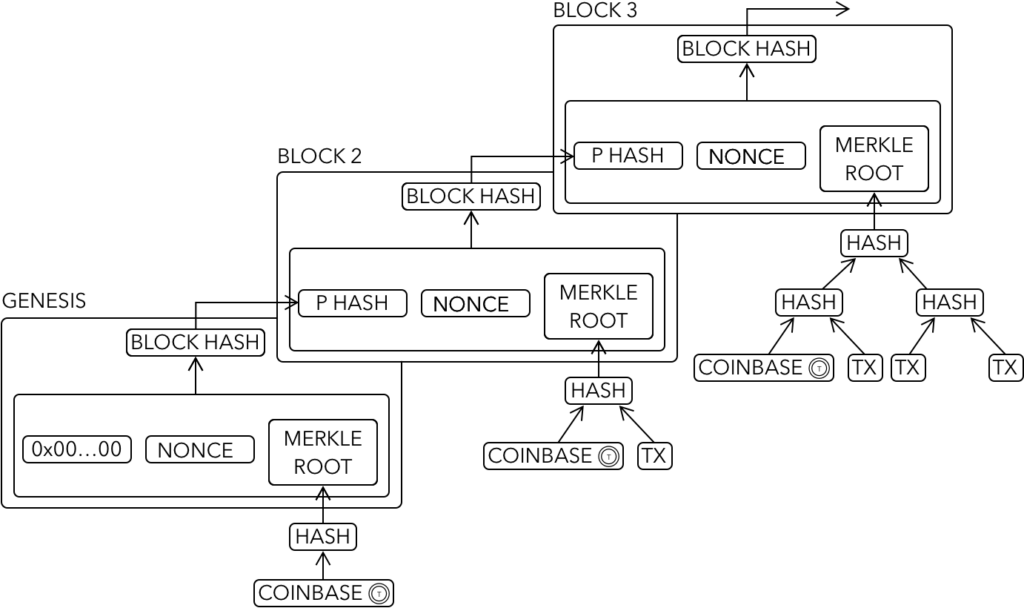
The use of hashing functions is central to cryptocurrencies (and DeFi). They are employed to verify the integrity of the entire history of transactions and are at the core of the mechanism that proves energy has been spent to generate each block of the blockchain. This is important because the chain with the most hashing power allocated is the one that is considered to be most trustworthy.
Encryption
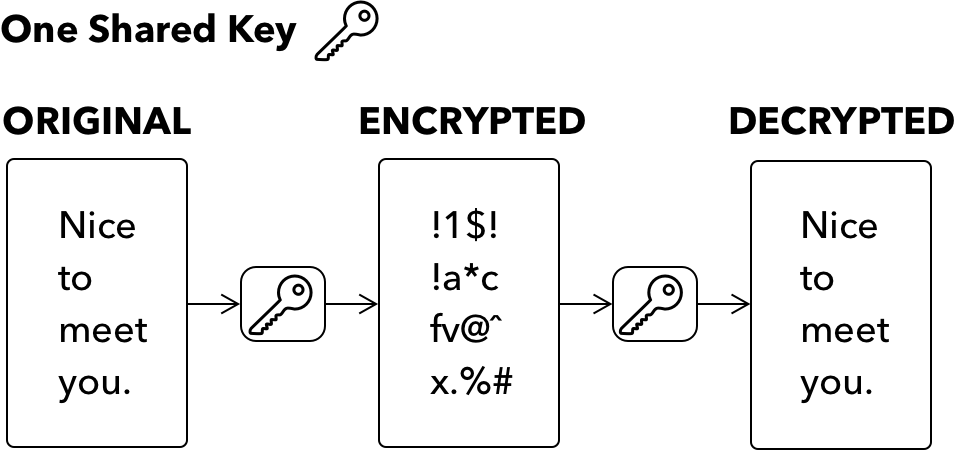
Encryption is the process of encoding information so that only those with access to a key or a secret can decode it. Encryption and decryption keys can be symmetric or asymmetric.
A symmetric key is used for both encryption and decryption, and both the sender and receiver must know this key before any encrypted communication.
With asymmetric keys, there is a key-pair typically denoted as the private and the public key. The receiver can use the public key to decrypt a message encrypted by the sender using the private key. It is also possible to encrypt a message using the public key so that only the private key can decrypt it.

Signatures
Cryptography also allows open messages to be signed by a private key and verified using a public key. This feature enables messages, including instructions (e.g., transfer x funds to y), to be authenticated and trusted.

Random number generators
Generating random numbers is critical to the entire cryptography field. For example, random numbers are required when generating new private/public key pairs, encrypting messages so that the same message can have different outputs, and mining new blockchain blocks that meet specific difficulty targets, among many other applications.
Applications
Combining all the previously described cryptographic components enables the creation of crypto identities, trusted blockchains, and smart contracts. This, in turn, allows the deployment of decentralized applications that can implement fungible and non-fungible tokens, exchanges, lending and borrowing platforms, etc.
These applications form ecosystems and communities that maintain close associations with the crypto designation. One example of such a community is the group of individuals who engage in Twitter discussions on topics related to this field and is referred to as Crypto Twitter (CT).